Cyber Security
GBS backups functions as a mechanism against cyber threats.
If your data is encrypted by a ransom or deleted by a wiper attack, we can restore it from a previous backup, stored in the night before the attack.
GBS protects the backups, so that the attacker cannot modify the data once the backup has been written.
Systems can be restored from a golden image, or from a permanent backup that was made days, weeks or months ago.
Backups are stored off-site, so that they are still available in case of a site disaster.
The backup system and its backups are protected from intruders, and the backup clients are protected from intrusion in case the backup server is compromised.
Security focus
We focus on security in the Linux systems that we deploy, using hardening and OpenSCAP security guidelines.
We focus on security in the backup mechanism’s that we deploy, using SSL encryption and PKI key management.
We run security audits on our and our customers systems.
Security in the backup has a few points of attention:
– Protect the backup client from intrusion
– Protect the data transfers by encrypting
– Protect the backup clients from intrusion via the backup server.
Security audits
Before deploying the backup, we can audit and review the backup applications for the same security standard as the backup server.
This safeguards the customer, with a second-opinion on the security state of their application/vendor.
The security audit is a logical extension of the backup deployment, because we have it the expertise that has been gathered for the backup security.
The backup server is designed with the highest security guidelines, therefore it makes sense to use the GBS security expertise to audit the connected appications, and identify its weak points. We check the application according the OpenSCAP and our internal Hardening guidlines.
Backup component security aspects:
Within the backup architecture, there are several components for our security focus:
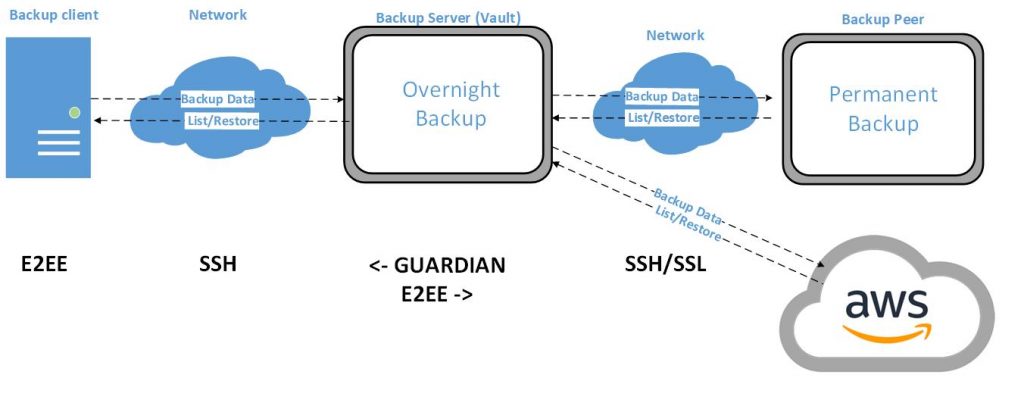
– Backup client (End to End backup, Hardening and Audit)
– Network traffic (encryption with SSL)
– Backup server (Hardening and the guardian security architecture)
Backup Security strategy
The strategy in the newest GBS3 release is to better protect the backups and the backup clients
The environment has changed, and we have to assume that backup clients no longer can be trusted.
Because the backup client could have been compromised by an intruder
Therefore the following limitations are in the backup mechanism:
– PKI keys for client access are locked with a passphrase.
– The client cannot modify his own backup.
– The client does not get access to the backup server
– All backups are scheduled from the Backup server
– The backup server is implemented and deployed as a Vault. No outside access
– Only use encrypted protocols.
– Protect the client system, don’t add a vulnerability. No agent software to be installed on the client
– E2EE mechanism for those cases where the Client does not trust the backup server
Linux Security
Linux security involves the correct deployment of a Linux server according established security guidelines.
GBS has a long history of deploying safe and secure systems.
For our Redhat/AlmaLinux deployments, we incorporate the guidelines from the “Red Hat Enterprise Linux 9
Security hardening” procedures.
This includes OpenSCAP security guidelines, utilities and scanner :